3 Architecture of the GSM network
During the early 1980s, analog cellular telephone systems were experiencing rapid growth in Europe, particularly in Scandinavia and the United Kingdom, but also in France and Germany. Each country developed its own system, which was incompatible with everyone else's in equipment and operation. This was an undesirable situation, because not only was the mobile equipment limited to operation within national boundaries, which in a unified Europe were increasingly unimportant, but there was a very limited market for each type of equipment, so economies of scale, and the subsequent savings, could not be realized.
The Europeans realized this early on, and in 1982 the Conference of European Posts and Telegraphs (CEPT) formed a study group called the Groupe Spécial Mobile (GSM) to study and develop a panEuropean public land mobile system. The proposed system had to meet certain criteria:
The developers of GSM chose an unproven (at the time) digital system, as opposed to the thenstandard analog cellular systems like AMPS in the United States and TACS in the United Kingdom. They had faith that advancements in compression algorithms and digital signal processors would allow the fulfillment of the original criteria and the continual improvement of the system in terms of quality and cost. The 8000 pages of the GSM recommendations try to allow flexibility and competitive innovation among suppliers, but provide enough guidelines to guarantee the proper interworking between the components of the system. This is done in part by providing descriptions of the interfaces and functions of each of the functional entities defined in the system.
From the beginning, the planners of GSM wanted ISDN compatibility in services offered and control signalling used. The radio link imposed some limitations, however, since the standard ISDN bit rate of 64 kbps could not be practically achieved.
Using the ITUT definitions, telecommunication services can be divided into bearer services, teleservices, and supplementary services. The digital nature of GSM allows data, both synchronous and asynchronous, to be transported as a bearer service to or from an ISDN terminal. Data can use either the transparent service, which has a fixed delay but no guarantee of data integrity, or a nontransparent service, which guarantees data integrity through an Automatic Repeat Request (ARQ) mechanism, but with a variable delay. The data rates supported by GSM are 300 bps, 600 bps, 1200 bps, 2400 bps, and 9600 bps [Har93a].
The most basic teleservice supported by GSM is telephony. There is an emergency service, where the nearest emergencyservice provider is notified by dialling three digits (similar to 911). Group 3 fax, an analog method described in ITUT recommendation T.30 [Har93b], is also supported by use of an appropriate fax adaptor. A unique feature of GSM compared to older analog systems is the Short Message Service (SMS). SMS is a bidirectional service for sending short alphanumeric (up to 160 bytes) messages in a storeandforward fashion. For pointtopoint SMS, a message can be sent to another subscriber to the service, and an acknowledgement of receipt is provided to the sender. SMS can also be used in a cellbroadcast mode, for sending messages such as traffic updates or news updates. Messages can be stored in the SIM card for later retrieval [Bal93].
Supplementary services are provided on top of teleservices or bearer services, and include features such as caller identification, call forwarding, call waiting, multiparty conversations, and barring of outgoing (international) calls, among others.

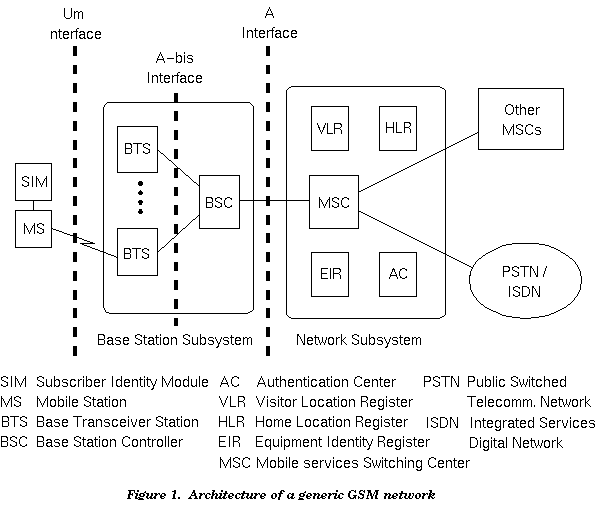
A GSM network is composed of several functional entities, whose functions and interfaces are defined. Figure 1 shows the layout of a generic GSM network. The GSM network can be divided into three broad parts. The Mobile Station is carried by the subscriber, the Base Station Subsystem controls the radio link with the Mobile Station. The Network Subsystem, the main part of which is the Mobile services Switching Center, performs the switching of calls between the mobile and other fixed or mobile network users, as well as management of mobile services, such as authentication. Not shown is the Operations and Maintenance center, which oversees the proper operation and setup of the network. The Mobile Station and the Base Station Subsystem communicate across the Um interface, also known as the air interface or radio link. The Base Station Subsystem communicates with the Mobile service Switching Center across the A interface.
The mobile equipment is uniquely identified by the International Mobile Equipment Identity (IMEI). The SIM card contains the International Mobile Subscriber Identity (IMSI), identifying the subscriber, a secret key for authentication, and other user information. The IMEI and the IMSI are independent, thereby providing personal mobility. The SIM card may be protected against unauthorized use by a password or personal identity number.
The Base Transceiver Station houses the radio tranceivers that define a cell and handles the radiolink protocols with the Mobile Station. In a large urban area, there will potentially be a large number of BTSs deployed. The requirements for a BTS are ruggedness, reliability, portability, and minimum cost.
The Base Station Controller manages the radio resources for one or more BTSs. It handles radiochannel setup, frequency hopping, and handovers, as described below. The BSC is the connection between the mobile and the Mobile service Switching Center (MSC). The BSC also translates the 13 kbps voice channel used over the radio link to the standard 64 kbps channel used by the Public Switched Telephone Network or ISDN.
The Home Location Register (HLR) and Visitor Location Register (VLR), together with the MSC, provide the callrouting and (possibly international) roaming capabilities of GSM. The HLR contains all the administrative information of each subscriber registered in the corresponding GSM network, along with the current location of the mobile. The current location of the mobile is in the form of a Mobile Station Roaming Number (MSRN) which is a regular ISDN number used to route a call to the MSC where the mobile is currently located. There is logically one HLR per GSM network, although it may be implemented as a distributed database.
The Visitor Location Register contains selected administrative information from the HLR, necessary for call control and provision of the subscribed services, for each mobile currently located in the geographical area controlled by the VLR. Although each functional entity can be implemented as an independent unit, most manufacturers of switching equipment implement one VLR together with one MSC, so that the geographical area controlled by the MSC corresponds to that controlled by the VLR, simplifying the signalling required. Note that the MSC contains no information about particular mobile stations - this information is stored in the location registers.
The other two registers are used for authentication and security purposes. The Equipment Identity Register (EIR) is a database that contains a list of all valid mobile equipment on the network, where each mobile station is identified by its International Mobile Equipment Identity (IMEI). An IMEI is marked as invalid if it has been reported stolen or is not type approved. The Authentication Center is a protected database that stores a copy of the secret key stored in each subscriber's SIM card, which is used for authentication and ciphering of the radio channel.
The International Telecommunication Union (ITU), which manages the international allocation of radio spectrum (among other functions) allocated the bands 890-915 MHz for the uplink (mobile station to base station) and 935-960 MHz for the downlink (base station to mobile station) for mobile networks in Europe. Since this range was already being used in the early 1980s by the analog systems of the day, the CEPT had the foresight to reserve the top 10 MHz of each band for the GSM network that was still being developed. Eventually, GSM will be allocated the entire 2x25 MHz bandwidth.
Since radio spectrum is a limited resource shared by all users, a method must be devised to divide up the bandwidth among as many users as possible. The method chosen by GSM is a combination of Time and FrequencyDivision Multiple Access (TDMA/FDMA). The FDMA part involves the division by frequency of the total 25 MHz bandwidth into 124 carrier frequencies of 200 kHz bandwidth. One or more carrier frequencies are then assigned to each base station. Each of these carrier frequencies is then divided in time, using a TDMA scheme, into eight time slots. One time slot is used for transmission by the mobile and one for reception. They are separated in time so that the mobile unit does not receive and transmit at the same time, a fact that simplifies the electronics.
In the rest of this section, the procedure involved in digitally transmitting a voice signal in a GSM network is examined, along with some of the features, such as discontinuous transmission and reception, used to improve voice quality, reduce the mobile unit's power consumption, and increase the overall capacity of the network.
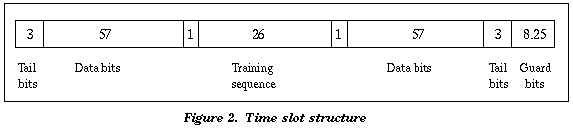
Each group of eight time slots is called a TDMA frame, which is transmitted every 4.615 ms. TDMA frames are further grouped into multiframes to carry control signals. There are two types of multiframe, containing 26 or 51 TDMA frames. The 26frame multiframe contains 24 Traffic Channels (TCH) and two Slow Associated Control Channels (SACCH) which supervise each call in progress. The SACCH in frame 12 contains eight channels, one for each of the eight connections carried by the TCHs. The SACCH in frame 25 is not currently used, but will carry eight additional SACCH channels when halfrate traffic is implemented. A Fast Associated Control Channel (FACCH) works by stealing slots from a traffic channel to transmit power control and handoversignalling messages. The channel stealing is done by setting one of the control bits in the time slot burst.
In addition to the Associated Control Channels, there are several other control channels which (except for the Standalone Dedicated Control Channel) are implemented in time slot 0 of specified TDMA frames in a 51frame multiframe, implemented on a nonhopping carrier frequency in each cell. The control channels include:
GSM is a digital system, so speech signals, inherently analog, have to be digitized. The method employed by ISDN, and by current telephone systems for multiplexing voice lines over high speed trunks and optical fiber lines, is Pulse Coded Modulation (PCM). The output stream from PCM is 64 kbps, too high a rate to be feasible over a radio link. The 64 kbps signal contains much redundancy, although it is simple to implement. The GSM group studied several voice coding algorithms on the basis of subjective speech quality and complexity (which is related to cost, processing delay, and power consumption once implemented) before arriving at the choice of a Regular Pulse Excited - Linear Predictive Coder (RPELPC) with a Long Term Predictor loop. Basically, information from previous samples, which does not change very quickly, is used to predict the current sample. The coefficients of the linear combination of the previous samples, plus an encoded form of the residual, the difference between the predicted and actual sample, represent the signal. Speech is divided into 20 millisecond samples, each of which is encoded as 260 bits, giving a total bit rate of 13 kbps.
Recall that the speech codec produces a 260 bit block for every 20 ms speech sample. From subjective testing, it was found that some bits of this block were more important for perceived speech quality than others. The bits are thus divided into three classes:
Class Ia 50 bits - most sensitive to bit errors
Class Ib 132 bits - moderately sensitive to bit errors
Class II 78 bits - least sensitive to bit errors
Class Ia bits have a 3 bit Cyclic Redundancy Code added for error detection. If an error is detected, the frame is judged too damaged to be comprehensible and it is discarded. It is replaced by a slightly attenuated version of the previous correctly received frame. These 53 bits, together with the 132 Class Ib bits and a 4 bit tail sequence (a total of 189 bits), are input into a 1/2 rate convolutional encoder of constraint length 4. Each input bit is encoded as two output bits, based on a combination of the previous 4 input bits. The convolutional encoder thus outputs 378 bits, to which are added the 78 remaining Class II bits, which are unprotected. Thus every 20 ms speech sample is encoded as 456 bits, giving a bit rate of 22.8 kbps.
To further protect against the burst errors common to the radio interface, each sample is diagonally interleaved. The 456 bits output by the convolutional encoder are divided into 8 blocks of 57 bits, and these blocks are transmitted in eight consecutive timeslot bursts. Since each timeslot burst can carry two 57 bit blocks, each burst carries traffic from two different speech samples.
Recall that each timeslot burst is transmitted at a gross bit rate of 270.833 kbps. This digital signal is modulated onto the analog carrier frequency, which has a bandwidth of 200 kHz, using Gaussianfiltered Minimum Shift Keying (GMSK). GMSK was selected over other modulation schemes as a compromise between spectral efficiency, complexity of the transmitter, and limited spurious emissions. The complexity of the transmitter is related to power consumption, which should be minimized for the mobile station. The spurious radio emissions, outside of the allotted bandwidth, must be strictly controlled so as to limit adjacent channel interference, and allow for the coexistence of GSM and the older analog systems (at least for the time being).
Minimizing cochannel interference is a goal of any cellular system, since it allows better service for a given cell size, or the use of smaller cells, thus increasing the overall capacity of the system. Discontinuous transmission (DTX) is a method that takes advantage of the fact that a person speaks less that 40 percent of the time in normal conversation [S+89], by turning the transmitter off during silence periods. An added benefit of DTX is that power is conserved at the mobile unit.
The most important component of DTX is, of course, Voice Activity Detection. It must distinguish between voice and noise inputs, a task that is not as trivial as it appears, considering background noise. If a voice signal is misinterpreted as noise, the transmitter is turned off and a very annoying effect called clipping is heard at the receiving end. If, on the other hand, noise is misinterpreted as a voice signal too often, the efficiency of DTX is dramatically decreased. Another factor to consider is that when the transmitter is turned off, there is a very silent silence heard at the receiving end, due to the digital nature of GSM. To assure the receiver that the connection is not dead, comfort noise is created at the receiving end by trying to match the characteristics of the transmitting end's background noise.
The mobile station measures the signal strength or signal quality (based on the Bit Error Ratio), and passes the information to the Base Station Controller, which ultimately decides if and when the power level should be changed. Power control should be handled carefully, since there is the possibility of instability. This arises from having mobiles in cochannel cells alternatingly increase their power in response to increased cochannel interference caused by the other mobile increasing its power. This in unlikely to occur in practice but it is (or was as of 1991) under study.
Ensuring the transmission of voice or data of a given quality over the radio link is only half the problem in a cellular mobile network. The fact that the geographical area covered by the network is divided into cells necessitates the implementation of a handover mechanism. Also, the fact that the mobile can roam nationally and internationally in GSM requires that registration, authentication, call routing and location updating functions exist in the GSM network.
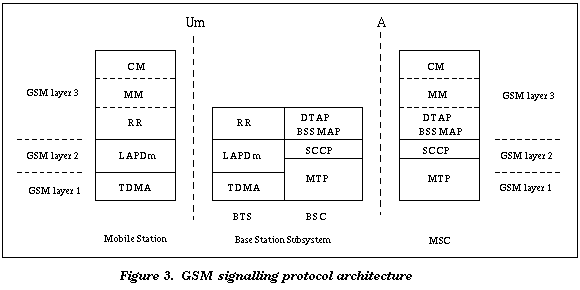
The signalling protocol in GSM is structured in three layers [Rah93, Aud88],
shown in Figure 3. Layer 1 is the physical layer, which uses the channel
structures discussed above. Layer 2 is the data link layer. Across
the Um interface, the data link layer uses a slight modification of the
LAPD protocol used in ISDN, called LAPDm. Across the A interface,
the lower parts of Signalling System Number 7 are used. Layer 3
is subdivided into 3 sublayers.
Signalling between the different entities in the network, such as between the HLR and VLR, is accomplished throught the Mobile Application Part (MAP). Application parts are the top layer of Signalling System Number 7. The specification of the MAP is complex. It is one of the longest documents in the GSM recommendations, said to be over 600 pages in length [Che91].
Described below are the main functions of the Mobility Management sublayer.
Handovers can be initiated by either the mobile or the MSC (as a means of traffic load balancing). During its idle time slots, the mobile scans the Broadcast Control Channel of up to 16 neighboring cells, and forms a list of the six best candidates for possible handover, based on the received signal strength. This information is passed to the BSC and MSC, and is used by the handover algorithm.
The algorithm for when a handover decision should be taken is not specified in the GSM recommendations. There are two basic algorithms used, both closely tied in with power control. This is because the BSC usually does not know whether the poor signal quality is due to multipath fading or to the mobile having moved to another cell. This is especially true in small urban cells.
The 'minimum acceptable performance' algorithm [Bal91] gives precedence to power control over handover, so that when the signal degrades beyond a certain point, the power level of the mobile is increased. If further power increases do not improve the signal, then a handover is considered. This is the simpler and more common method, but it creates 'smeared' cell boundaries when a mobile transmitting at peak power goes some distance beyond its original cell boundaries into another cell.
The 'power budget' method [Bal91] uses handover to try to maintain or improve a certain level of signal quality at the same or lower power level. It thus gives precedence to handover over power control. It avoids the 'smeared' cell boundary problem and reduces cochannel interference, but it is quite complicated.
The MSC provides the interface between the GSM mobile network and the public fixed network. From the fixed network's point of view, the MSC is just another switching node. However, switching is a little more complicated in a mobile network since the MSC has to know where the mobile is currently roaming - and in GSM it could even be roaming in another country. The way GSM accomplishes location updating and call routing to the mobile is by using two location registers: the Home Location Register (HLR) and the Visitor Location Register (VLR).
Location updating is initiated by the mobile when, by monitoring the Broadcast Control Channel, it notices that the locationarea broadcast is not the same as the one previously stored in the mobile's memory. An update request and the IMSI or previous TMSI is sent to the new VLR via the new MSC. A Mobile Station Roaming Number (MSRN) is allocated and sent to the mobile's HLR (which always keeps the most current location) by the new VLR. The MSRN is a regular telephone number that routes the call to the new VLR and is subsequently translated to the TMSI of the mobile. The HLR sends back the necessary callcontrol parameters, and also sends a cancel message to the old VLR, so that the previous MSRN can be reallocated. Finally, a new TMSI is allocated and sent to the mobile, to identify it in future paging or call initiation requests.
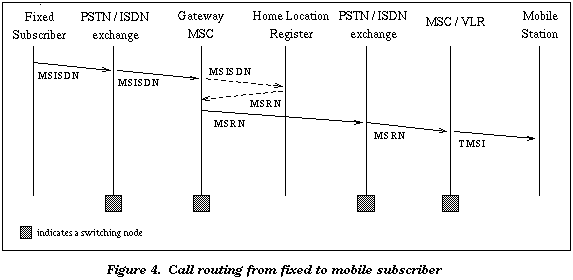
With the above locationupdating procedure, call routing to a roaming mobile
is easily performed. The most general case is shown in Figure 4 [Aud88],
where a call from a fixed network (Public Switched Telecommunications Network or
Integrated Services Digital Network) is placed to a mobile subscriber.
Using the Mobile Subscriber's telephone number (MSISDN, the ISDN
numbering plan specified in the ITUT E.164 recommendation), the call
is routed through the fixed land network to a gateway MSC for the GSM network
(an MSC that interfaces with the fixed land network, thus requiring
an echo canceller). The gateway MSC uses the MSISDN to query the Home
Location Register, which returns the current roaming number (MSRN). The MSRN
is used by the gateway MSC to route the call to the current MSC (which is
usually coupled with the VLR). The VLR then converts the roaming number
to the mobile's TMSI, and a paging call is broadcast by the cells under
the control of the current BSC to inform the mobile.
Since the radio medium can be accessed by anyone, authentication of users to prove that they are who they claim to be, is a very important element of a mobile network. Authentication involves two functional entities, the SIM card in the mobile, and the Authentication Center (AC). Each subscriber is given a secret key, one copy of which is stored in the SIM card and the other in the Authentication Center. During authentication, the AC generates a random number that it sends to the mobile. Both the mobile and the AC then use the random number, in conjuction with the subscriber's secret key and a ciphering algorithm called A3, to generate a number that is sent back to the AC. If the number sent by the mobile is the same as the one calculated by the AC, the subscriber is authenticated.
The above calculated number is also used, together with a TDMA frame number and another ciphering algorithm called A5, to encipher the data sent over the radio link, preventing others from listening in. Enciphering is an option for the very paranoid, since the signal is already coded, interleaved, and transmitted in a TDMA manner, thus providing protection from all but the most persistent and dedicated eavesdroppers.
Another level of security is performed on the mobile equipment, as opposed to the mobile subscriber. As mentioned earlier, each GSM terminal is identified by a unique International Mobile Equipment Identity (IMEI) number. A list of IMEIs in the network is stored in the Equipment Identity Register (EIR). The status returned in response to an IMEI query to the EIR is one of the following:
In this paper I have tried to give an overview of the GSM system. As with any overview, and especially one covering a standard 8000 pages long, there are many details missing. I believe, however, that I gave the general flavor of GSM and the philosophy behind its design. It was a monumental task that the original GSM committee undertook, and one that has proven a success, showing that international cooperation on such projects between academia, industry, and government can succeed. It is a standard that ensures interoperability without stifling competition and innovation among suppliers, to the benefit of the public both in terms of cost and service quality. For example, by using Very Large Scale Integration (VLSI) microprocessor technology, many of functions of the mobile station can be built in one chipset, resulting in lighter, smaller, and more energyefficient terminals.
Telecommunications are evolving towards personal communication networks, whose objective can be stated as the availability of all communication services anytime, anywhere, to anyone, by a single identity number and a pocketable communication terminal [Win93]. Having a multitude of incompatible systems throughout the world moves us farther away from, not closer to, this ideal. The economies of scale created by a unified system are enough to justify its implementation, not to mention the convenience to people of carrying just one communication terminal anywhere they go, regardless of national boundaries.
The GSM system, and its twin system operating at 1800 MHz, called DCS1800, are a first approach at a true personal communication system. The SIM card is a novel approach that implements personal mobility in addition to terminal mobility. Together with international roaming, and support for many other services such as data transfer, fax, Short Message Service, and supplementary services, in addition to telephony, GSM comes close to fulfilling the requirements for a personal communication system: close enough that it is being used as a basis for the next generation of communication technology in Europe.
Another point where GSM has shown its commitment to openness, standards and interoperability is the compatibility with the Integrated Services Digital Network (ISDN) that is evolving in most industrialized countries, and Europe in particular (the socalled EuroISDN). GSM is the first system to make extensive use of the Intelligent Networking concept in ISDN, in which services like 800 numbers are concentrated and handled from a few centralized service centers, instead of being distributed over every switching center in the country. This is the concept behind the use of the various registers such as the HLR. In addition, the signalling between these functional entities uses Signalling System Number 7, an international standard already used in many countries and specified for ISDN.
GSM is a very complex standard, but that is probably the price that must be paid to achieve the level of integrated service and quality offered while subject to the fairly severe restrictions imposed by the radio environment.